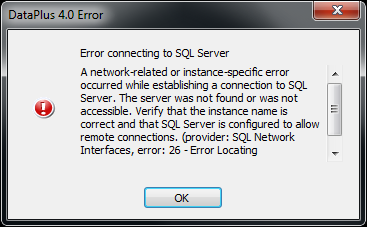
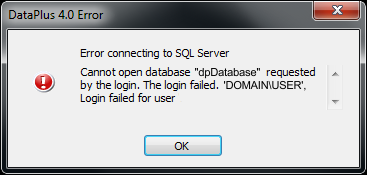
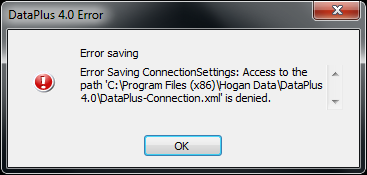
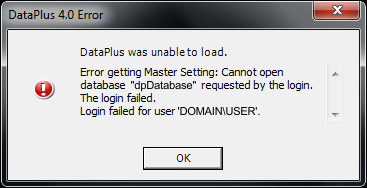
Knowledge Base
Logins must be mapped to database user accounts in order to work with database objects. Database users can then be added to database roles, inheriting any permission sets associated with those roles. All permissions can be granted.
You must also consider the public role, the dbo user account, and the guest account when you design security for your application.
The public Role